TECH NEWS
How to handle cyber incidents and meet regulatory requirements
As the digital landscape continues to evolve, so does the prevalence and sophistication of cyber incidents.
June 17, 2024

Europe’s finance sector, deeply entwined with information and communication technology (ICT), has not been spared in the face of this growing cyber onslaught. Recent years have witnessed a considerable surge in such incidents, proving highly disruptive to services and posing grave threats to the security, integrity, and confidentiality of data across the industry. Such an upward trend underscores not just the vulnerabilities in institutions’ ICT infrastructure, but also the severe damage capable of being inflicted by malicious cyber criminals. The ceaseless cybersecurity hurdles impose an escalating burden on businesses and policymakers within the European financial landscape, as they strive to stay ahead of the inestimable risks that such incidents bring along.
In the following paper, we will explain the new requirements of CSSF 24/847 and SEC regulations, and provide a comprehensive guideline for establishing a stringent incident response.
European banks and large companies have become prime targets for cyberattacks, especially since the onset of the armed conflict and the war against Ukraine. According to a report by IBM, the worldwide average financial impact of a data breach in 2023 escalated to an alarming USD 4.45 million – a notable 15% increase from the cost witnessed three years prior. The time it took to identify and contain a breach was a staggering average of 277 days, underscoring the extensive duration these incidents can cripple business operations.
 In response to escalating ICT and security threats within a highly connected, global financial ecosystem, the CSSF unveiled the Circular CSSF 24/847 on 5 January 2024. This revision of its reporting guidelines for ICT-related incidents represents a strategic move towards bolstering understanding and effectively categorizing such incidents.
In response to escalating ICT and security threats within a highly connected, global financial ecosystem, the CSSF unveiled the Circular CSSF 24/847 on 5 January 2024. This revision of its reporting guidelines for ICT-related incidents represents a strategic move towards bolstering understanding and effectively categorizing such incidents.
According to the circular, supervised entities are required to categorize ICT-related incidents based on criteria defined in DORA, including:
- the number of affected clients or transactions,
- the duration of the incident,
- the geographical regions affected,
- any data losses,
- the impact on mission-critical services, and
- the financial impact.
If an entity’s assessment, based on these criteria, deems an ICT-related incident as “major”, it is then classified as such. If the assessment does not provide a clear classification, the incident must be reported to the CSSF. Incidents must be classified promptly after detection, and no later than 24 hours after detection. If more time is needed, the entity must give a valid reason to the competent authority.
Any successful malicious unauthorized access to the network and information systems or a classified major incident must be reported within 24 hours to the CSSF.
The incident notification protocol involves three stages:
- a) Initial Notification: This is the first alert that is sent out when a major ICT-related incident is detected and recognized. The message would typically include the basic details about the breach – its nature, when it was discovered, the immediate effect, and any other initial information that could be critical in understanding and addressing the situation. The purpose of this initial notification is to alert the authorities to then mobilize their response to the incident.
- b) Intermediate Notification: Following the initial notification, a more comprehensive report detailing the cause, classification, and impact of the incident would be provided. This notification could include information about the origin of the incident, what parts of the system were affected, and its potential consequences. These notifications may be updated regularly as more information becomes available, or upon specific request by the CSSF. The main aim here is to monitor the evolution of the incident and to guide the response strategies.
- c) Final Notification: Once the primary analysis of the root cause of the incident has been completed, a final notification is issued. This notification would include the detailed root cause analysis report, the actual impact figures replacing any initial estimates given and any mitigation measures that have been put in place. This final notification is sent regardless of whether these mitigation measures have been fully implemented. This report also allows the supervised entities to include any follow-up and additional information they deem relevant to the incident. The final notification acts as the conclusion of the incident report, providing a full overview of the incident and its effects on the system.

In July 2023, the US Securities and Exchange Commission (SEC) introduced new regulations requiring that registrants promptly report cybersecurity incidents and include details about their management of cybersecurity risks, their strategic approaches, and their governance in their annual reports. These rules apply to almost all registrants who are obligated to submit regular reports to the SEC, such as Form 10-K and Form 20-F, including smaller reporting companies, emerging growth companies, and foreign private issuers.
In the case of domestic registrants, should there be a substantial cybersecurity incident, they must disclose this within four business days on Form 8-K once the incident has been deemed significant and must divulge the following aspects related to the major incident: its nature, scope, and timing; the significant impact or the potential notable impact on the registrant’s financial status and operating results.
Foreign private issuers are also expected to promptly disclose any significant cybersecurity incident, reporting it on Form 6-K once they determine the incident is of substantial importance. They are to furnish on Form 6-K details of significant cybersecurity incidents that they have disclosed or publicized in a foreign jurisdiction, any stock exchange, or to their security holders.
A recent example, in their regulatory filing, Microsoft revealed that email accounts of some of its highest-ranking executives were infiltrated by Nobelium, a Russian intelligence group. This is the same group that managed to breach the systems of SolarWinds in 2020, one of the most impactful cyber-attacks in history. The supply-chain attack on the company that produces software for managing networks, systems, and infrastructure. The hackers, successfully managed to breach several US government departments, including Treasury and Commerce. They conducted a sophisticated operation wherein they infected a network management software update from SolarWinds, which was then used by approximately 18,000 customers globally. The company not only had to survive and overcome this incident, but also had to assume the fines imposed by the regulators, as SEC charged the company and Chief Information Security Officer with fraud, internal control failures.
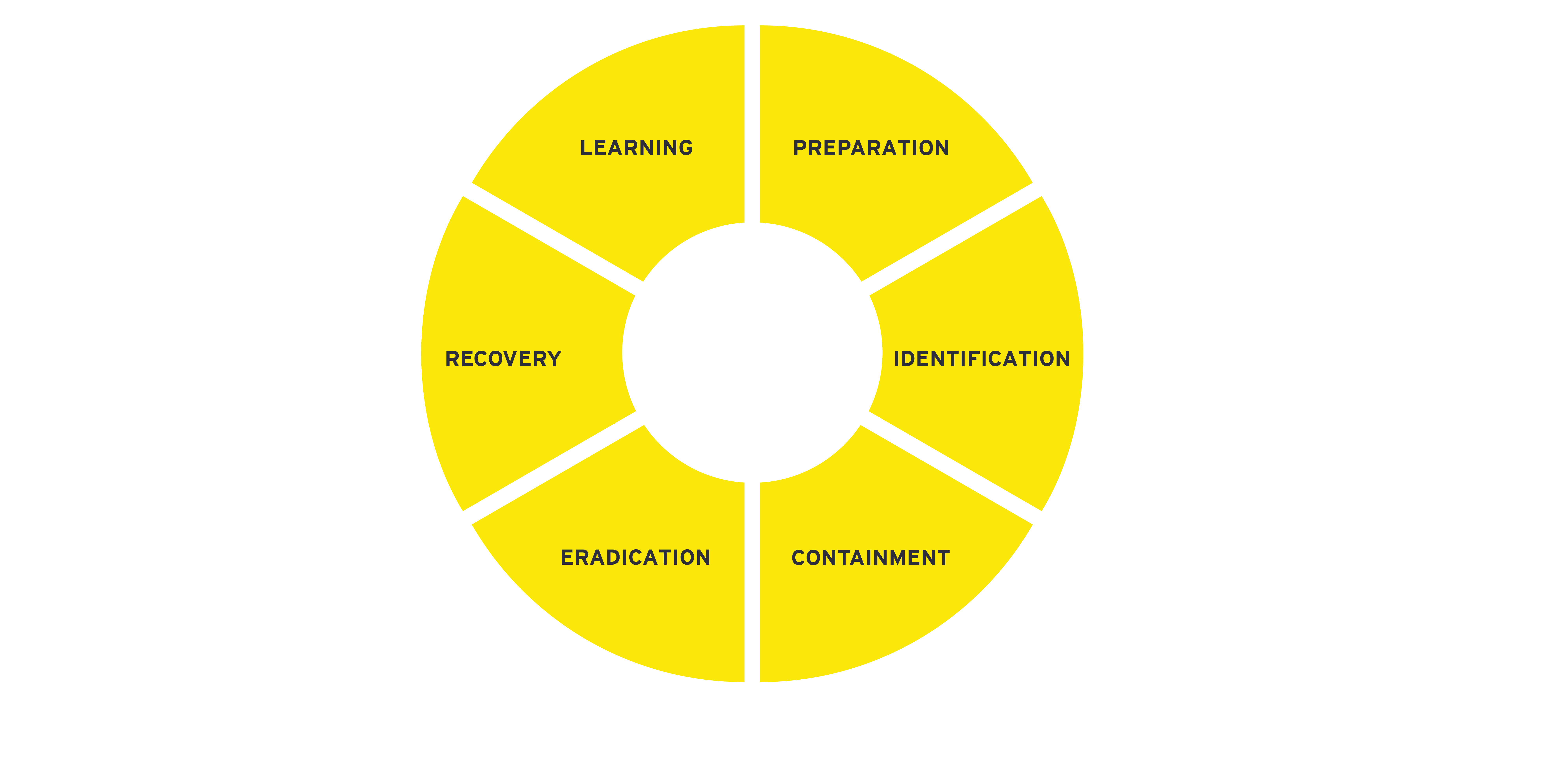
While it’s a complex task, being prepared for a cyber incident can make all the difference in how much a company will lose – whether that’s in money, time, or trust. It’s better to be proactive rather than reactive. After all, not every cybersecurity incident ends in disaster or has to be reported – but without an effective incident response plan, it might as well. In the labyrinth of cybersecurity, being prepared for all possible junctures is key to safely navigating through it. The creation of a robust incident response strategy hinges on six critical stages, each playing a vital role in managing an incident holistically. Firstly, preparation entails establishing an incident response team, defining roles, identifying what constitutes an incident, and developing an incident response plan that includes procedures for recognizing, reporting, and evaluating incidents. Secondly, the identification phase involves the detection and assessment of a potential incident by monitoring systems and analyzing alerts. This is followed by containment, where the impact of the incident is minimized by isolating the affected systems. Eradication is next, where the root cause of the incident is identified, eliminated from the system, and further preventive measures are taken. Recovery then follows, involving the restoration of the systems to their initial function, after ensuring they are threat-free. Lastly, “lessons learned” is a review and reflective stage, entailing comprehensive incident documentation, assessing areas of improvement, and updating the response plan to buffer against future incidents.
In conclusion, the constantly evolving and increasingly advanced cybersecurity threats in today’s digital age necessitate not only an effective and swift incident response strategy but also a culture of strong preemptive measures within organizations. The need for prompt reporting of such incidents to relevant regulatory bodies adds a noteworthy layer of complexity. This is essential not only for regulatory compliance, but it also serves to inform and enhance industry-wide defense mechanisms by sharing valuable insights.
EY is uniquely positioned to assist organizations in fostering this much-needed robust incident response strategy. We tailor these strategies to each organization’s unique needs, ensuring compliance with notification requirements. In the dynamic landscape of cybersecurity, a formidable defense is crafted from a synergy of robust preventative measures, strategic incident responses, and judicious reporting, all customized to the needs of the organization.
Authors:
|
Alexandre Minarelli EY Luxembourg Partner, Technology Risks |
Guillaume Carballo EY Luxembourg Partner, Cybersecurity Leader |
Imane Chekirine EY Luxembourg Manager, Risk Consulting |