DIGITAL SOLUTIONS
How to protect your industrial assets ?
Without proper security, organizations can be infiltrated by hackers and terrorists, or simply left exposed by negligence.
August 22, 2022

As industrial IoT expands, equipment and systems are increasingly connected and must be protected from new digital threats. Without proper security, organizations can be infiltrated by hackers and terrorists, or simply left exposed by negligence.
Securing IT systems in industrial organizations is critical, and becoming more important daily as the digital transformation increasingly connects systems and equipment.
Internal exploitation
WALLIX Bastion helps you coordinate IT departments with traditional ICS (Industrial Control System) teams’ activities thanks to features that enable you to manage, monitor, trace, and secure privileged users
Challenges
- Traceability of maintenance and exploitation activity
- Secure access to critical components
- Traceability and accountability of privileged Industrial Control
Solutions
WALLIX Bastion to centralize, control and trace identity and access on engineering stations, SCADA, IHMs, etc…
Benefits
- Accountability of maintainers and traceability of activity
- Removal of shared accounts: the operator no longer knows the target’s authentication information
- Securing access from IT
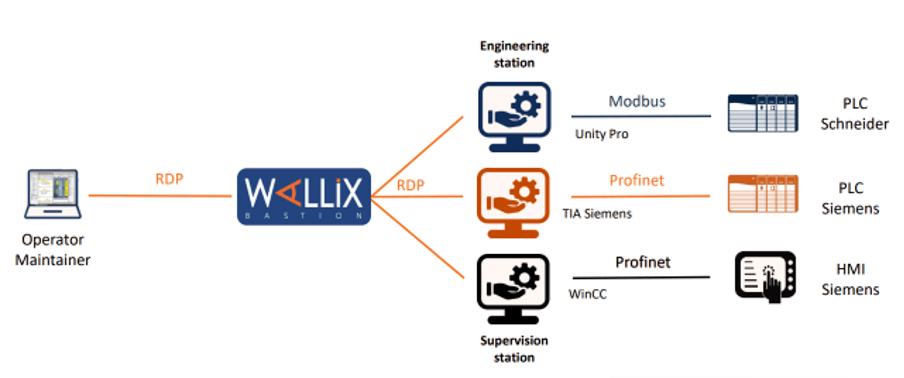
External Maintenance
Control access by remote maintenance workers and maintain operational efficiency and comprehensive IT-OT security. Maintainers of industrial systems need mobility and fast access to the equipment they supervise while controlling access authentication.
WALLIX provides a secure external user connection to facilitate software upgrades, periodic maintenance, or any support activity within OT networks.
The WALLIX Bastion offers robust access management for Windows-based controller stations, SSH-based systems, and third-party applications.
Challenges
- Remove and centralize remote access tools
- Ensure completely secure access to critical resources from outside the enterprise
Solutions
- WALLIX Bastion with the WALLIX Access Manager web portal dedicated to external access
- Security can be enhanced with native MFA and approbation workflows
- Multi-tenant portal
Benefits
- Secure end-to-end access via a web portal
- Mobile access (tablet/smartphone)
- Easy to use for any type of population
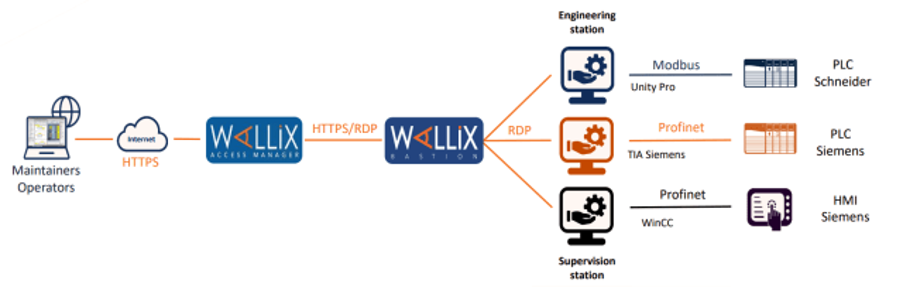
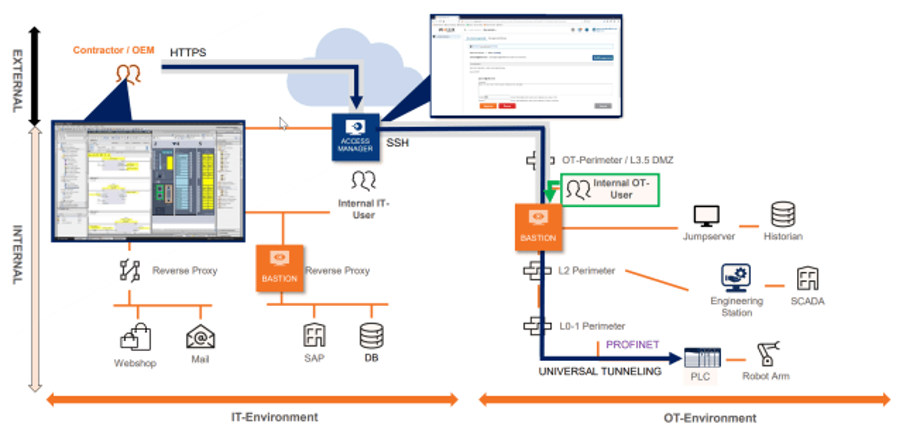
Below is the access workflow and associated diagram of external users (using their own workstation) to the enterprise internal engineering station:
-
- Connection via browser is established
- The user is authenticated (multi-factor can be enforced)
- The target system (engineering station) is selected via GUI
- The approval workflow is started
- A secure primary connection to the bastion is established
- Secure secondary connection to engineering station with TIA portal is established (agentless)
- PLC is selected and the connection is established natively via OT protocol (Porfinet is this example), user is logged in (SSO) and applicable rule sets are established
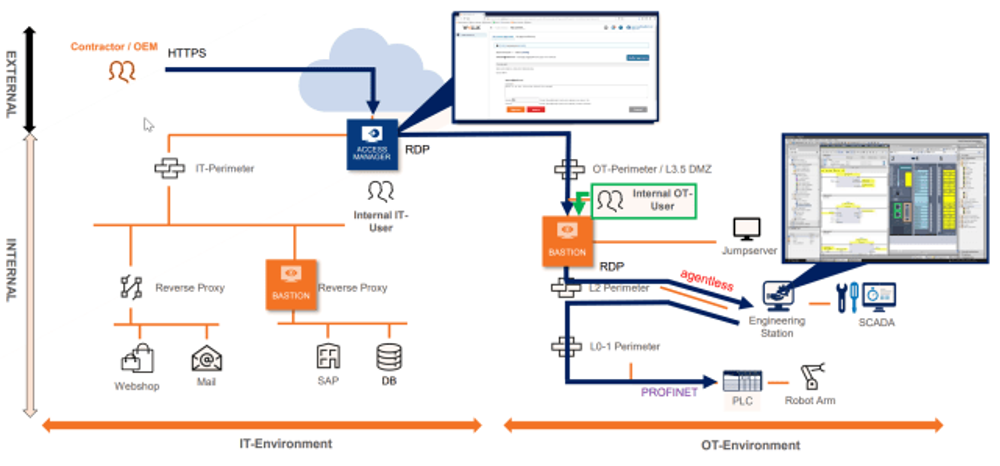
External maintenance through the use of OT tunnelling
Unique to WALLIX, Universal Tunneling allows you to benefit from the power and simplicity of WALLIX Bastion all while simplifying user experience.
Connect directly to PLCs without going through a bounce server; we encapsulate industrial protocols (Modbus, Profinet, BacNet, EtherCAT, etc.) in an SSH tunnel to ensure the control and traceability of each session. No more costly bounce servers, you access your resources directly from your usual work environment.
Challenges
- Promote the adoption of the PAM solution for an OT audience
- Avoid having to connect to an intermediate machine (jump host) hosting the PLC maintenance application
Solutions
- WALLIX Universal Tunneling to support industrial protocols through the Bastion
Benefits
- Reduced TCO: no need for Jump Servers
- Traceability of connections.
- Enforced forensic with the availability of Session PCAPs
- The operator works as easily as without a Bastion
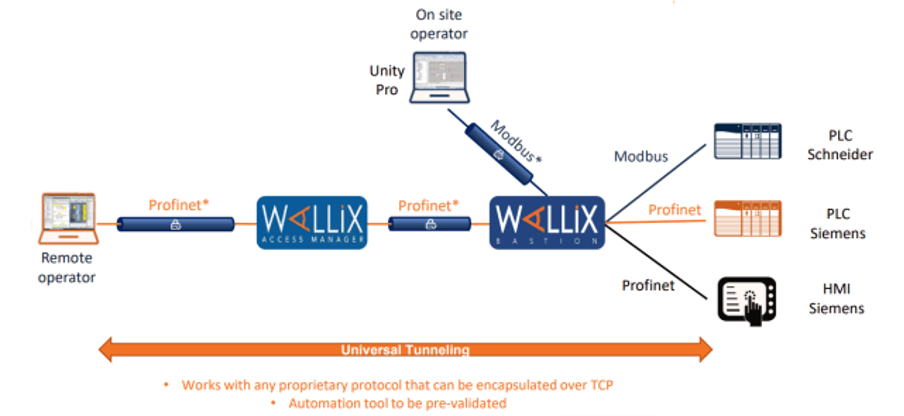
Below is the access of an external user (remote workstation) to OT component:
-
- connection via browser is established
- User is authenticated
- The target system (PLC) is selected via GUI
- The approval workflow is started
- A secure tunnel (universal tunnelling) via bastion to PLC is established
- TIA Portal is executed via Engineering Workstation
- PLC is selected and the connection is established via the existing tunnel, the user is logged in (SSO) and an applicable set of rules is established.
If you like this article, discover other cybersecurity articles on Blog – Excellium Services (excellium-services.com)
Author: Pierre Ruaro | LinkedIn